2d4a2b84:829b0aaa
reacted
a minute ago
⚡
622ba6c7:af4482be
posted
23 minutes ago
Where's the Sun? ;)
3eba5ef4:751f23ae
posted
24 minutes ago
Fuzzing CKB-VM Into Shape: The Hidden Work Behind Meepo
Do you know that a big part of Meepo’s development time went into fuzzing test, rather than writing new features?
To ensure the reliability and consistency of CKB-VM upgrades on mainnet and testnet, we fuzzed both valid and invalid transactions to catch any subtle compatibility issues early.
The goal was to:
- Ensure stable and consist transaction execution
- Prevent panics
- Verify compatibility in aspects like cycle consumption and error handling across different versions and hardforks
Here’s how fuzzing helped.
1/ Initial Verification: Transaction Replay 🔁
We began by replaying historical on-chain transactions (via `replay`) from mainnet and testnet to check if `cycle` consumption remained consistent in the upgraded CKB-VM.
This caught several mismatches:
https://image.nostr.build/72d9d82dea118a96f7001cdaf76acd272e2e0ec87f40eeb0d82214d6db7f6aba.png
As the chain only contains valid transactions, this method verifies past compatibility but not future cases. To broaden coverage, we turned to fuzzing to simulate diverse transaction inputs and assess compatibility across versions, including error handling in invalid transactions.
2/ First Fuzzing Attempt 🧪
We compared the execution results of `data0` and `data1` of the pre- and post-upgrade VM versions:
https://image.nostr.build/2604ddaf8c015682330ab1cc363eb4f030c8e13dd7d7aa91e418ca7a3780a178.png
However, most generated test cases were invalid. The test only compared whether the errors matched, but skipped the cycle consumption for valid cases—not enough to meet our goals.
3/ Improved Fuzzing 🔧
To increase valid transaction input coverage, we refined the strategy:
- Corpus Optimization: Added valid transaction data from CKB-VM tests and CKB debugger binaries to the fuzzing corpus.
- Input Filtering: Modified fuzzing logic to only keep valid transactions in the corpus, further increasing the frequency of valid samples and enhancing `cycle` verification.
https://image.nostr.build/fbe59fd5933449e7babf2ea5a3d6b834336f853251804c9a66fb6c81932a0ed9.png
4/ Findings 😃
Improved fuzzing uncovered bugs, including:
- Crash caused by an invalid syscall parameter. Fix: https://github.com/libraries/ckb/commit/38279e118d3fda3c52f1d47d2062f80e19a2d523
- Instruction reordering led to mismatched `cycle` cost and memory out-of-bounds errors. Fix: https://github.com/libraries/ckb/commit/ea4aea7fa4cd87ce5df6dee6616466458ff5a86e
- Inconsistent error handling due to mismatched `DataPieceId` behavior. Fix: https://github.com/libraries/ckb/commit/af87dd355a653eaca19a643866300cc5cd907cf5
- Address truncation in x64. Fix: https://github.com/nervosnetwork/ckb-vm/commit/f6df535bbf8864fd14684c133b1aa8026a0b0868
- Inconsistencies in memory tracking. Fix: https://github.com/nervosnetwork/ckb-vm/commit/065a6457d06aa17da4f7dfa1954a2601fc7d288b
All issues were reproduced, analyzed, and added to the test corpus and the fuzzing crash directory for regression testing.
5/ Went Deeper: ISA-Level Fuzzing 🦾
In addition to compatibility testing, we fuzzed the instruction set to prevent unexpected VM panics.
See: https://github.com/nervosnetwork/ckb-vm-fuzzing-test
6/ Fuzzing isn’t flashy, but it pays off. 🛡️
As we know reliability is what gives developers confidence to build.
We’ll gladly keep things safe and steady—and maybe a little boring—so you don’t have to. 😎
8/ Reference Links 🔗
Fuzzing and tools:
- https://github.com/nervosnetwork/ckb-vm/tree/develop/fuzz
- https://github.com/libraries/schedfuzz
- https://github.com/nervosnetwork/ckb-vm-fuzzing-test/
On VM 2:
- https://github.com/nervosnetwork/rfcs/blob/master/rfcs/0049-ckb-vm-version-2/0049-ckb-vm-version-2.md
58937958:545e6994
posted
30 minutes ago
Sorry! I made a mistake in my post.
It looks like I tagged the wrong account.
nostr:nevent1qvzqqqqqqypzqkyn09vqxm8da92mykujjkpczs969h4vhrge88kerfqmuf29u6v5qyxhwumn8ghj77tpvf6jumt9qys8wumn8ghj7un9d3shjtt2wqhxummnw3ezuamfwfjkgmn9wshx5uqpr4mhxue69uhhyetvv9ujumn0wd68ytnhd9ex2erwv46zu6nsqy28wumn8ghj7un9d3shjtnyv9kh2uewd9hszythwden5te0wghxkmm2d9exztnfduq3samnwvaz7tmjv4kxz7fwwdhx7un59eek7cmfv9kqzrthwden5te0dehhxtnvdakqz9nhwden5te0wfjkccte9ec8y6tdv9kzumn9wsq3vamnwvaz7tmjv4kxz7fwdehhxarj9e3xzmnyqqsxzxyc9nznataf5pqdajdz4ln67fckzd3d6zp63dzwfvl32fpnx7cpu7pj6
58937958:545e6994
posted
32 minutes ago
🌊Bitcoin Seoul 2025🌊
Bitcoin crosses borders.
That day, as I watched Bitcoin payments for my handmade goods fly in again and again,
I felt that more deeply than ever.
Some images in this video are from PromenadeCastle / @Oree
https://video.nostr.build/1a4de9f2132a69e456cf96725c3c119f87289cde099d4ad3d25d5777710ad8cb.mp4nostr:npub1evz2dan8p8rw9gc2csaz6dhgj2na77xxwhxsynlku60du2lul94qakqkgh
8c33bebb:3a101285
reposted
an hour ago
{"id":"5e0b2a1617c5a4a4fce4860b1dcf35278e9d3009e8af680b83b971b34c5f0559","pubkey":"a401dd1742ee4afd4a6fbc798290115497893133dd5069195f79e2ecc4b3b068","created_at":1748716578,"kind":1,"tags":[],"content":"“If I had maintained an oath of silence my whole lifelong for safety, I would still have suffered, and I would still die”\n\nYour voices are powerful and are changing the world.\n\nI was just deplatformed by Meta. \n\nWill that finally make me silent?\n\nNever.\nhttps://blossom.primal.net/538cada4679cb9cb26290a9f59890b4c643beb41bc83a708bf25b8a6f53623bf.mp4","sig":"e8bbea021c8eaf80a89812f1b79f648144eaf45aecd22e38e0fffbb11c294c9684900b827da5790670e1f3167519c6d46927fb6e46f194f08816c72cb1f6979c"}
untreu
posted
an hour ago
8c33bebb:3a101285
reposted
an hour ago
{"id":"61e9338f1f88832bb06af5ca936cc089130f20c47c272c8006565b489fa9d537","pubkey":"165b9d37a28903103af9ad24036bdc54270882c01add515791fc9666167cfac1","created_at":1749618497,"kind":1,"tags":[["p","2a89078b66f39e95cf9dbab2d074fd6197efb46de289b9530b7374c813e796a7","wss://relay.mostr.pub"],["e","73dffe80c51983e92135e8bd2ce1b5097bddda3b1ed9007868f5e0005ee34123","wss://relay.mostr.pub","root","2a89078b66f39e95cf9dbab2d074fd6197efb46de289b9530b7374c813e796a7"]],"content":"The first 3 days of protests were marked with an insanely high number of federal agents working as provocateurs. \n\nWhen the police just stand around and let a guy with his face covered do burnouts around a burning car left in rhe centre of the intersection so that journalists can take photos of the burning car and police in the background etc. \nShits just so obvious. \nThey used federal agents carrying Mexican flags going around starting fires smashing windows trying to encourage people to loot and riot. \n\nIf you watched any of the Livestreams of the actual protests you'd see it's two completely different crowds. \nObviously now though all the opportunists have come out to join in on the looting and rioting but that's the whole point. \n\nProblem reaction solution. \nTrump being the Zionist pedophile he is, used a false flag to justify bringing in the national guard, which caused the problem. \nNow people are reacting by blaming Mexicans or migrants in general. \nnext comes solution. ","sig":"7d297dc62f2ab5f83233cf22a828a788c675f4e04a1afc8037d2ee7795de05a63212f0c8712fee7416d0ebc5e8552ac6ba865f8a71525fdb4908efeccc72b5f4"}
7e68f253:892b7432
reacted
2 hours ago
🫂
41b3a7b5:de0463d6
posted
2 hours ago
Obviously ❗️
nostr:nevent1qqs2tc30v7a5fd6w2upjpvm9th9zju7c8s6cnuaaqzymg5rnsqfup6spzemhxue69uhhyetvv9ujuurjd9kkzmpwdejhg5czers
391819e2:e5e8a248
reacted
3 hours ago
+
a3ce3b17:b7588d3c
reposted
4 hours ago
{"id":"46f5ecbf7a7d008bc590c5a533558d044da58d9d0564b14388c5401c8924c45d","pubkey":"0018b7ee33fb253843639c62e292fec700a69a93b08ee374c5bda971c9b39564","created_at":1749451724,"kind":1,"tags":[["t","Nostr"],["r","wss://filter.nostr.wine/"],["r","wss://nos.lol/"],["r","wss://nostr-pub.wellorder.net/"],["r","wss://nostr.bitcoiner.social/"],["r","wss://nostr.mom/"],["r","wss://nostrelites.org/"],["r","wss://premium.primal.net/"],["r","wss://atlas.nostr.land/"]],"content":"Round 2 with the legend Dr. Anthony Chaffee just went live on his channel!\n\nUnloaded a pallet of orange pills and a couple sneaky purple pills to his 500K subscribers.\n\nTake 30 seconds to leave a #Nostr comment under his video to help convince him to join us 👀👇\nhttps://youtu.be/kMmvqNnZMbM","sig":"93c4577dda61c07ccb1b5b9b7dccd7787da04a07db39e22d611d5c7f77580ea6e8300cc8c43325276193a2ed4b36b3151746fa2b23c069dd5290506311afe527"}
7eb44b7c:d8d5552f
posted
4 hours ago
Bankers: “Quantum computing is a threat to #Bitcoin”
Bitcoin:


f4e8a832:2886faa8
reacted
5 hours ago
👍
bitcoinpoorguy
posted
5 hours ago

0018b7ee:c9b39564
posted
5 hours ago
the US government is just fixing our vayu energy, guys https://blossom.primal.net/9635cebcb5af6b18ab5b4aa83a9a637e5de7fd3c22bc82786c2ca60901528bfd.mp4
841b017d:8bf0ee39
reacted
5 hours ago
💜
3589b793:ad53847e
reacted
5 hours ago
+
8f9efe5e:665fe6da
posted
5 hours ago
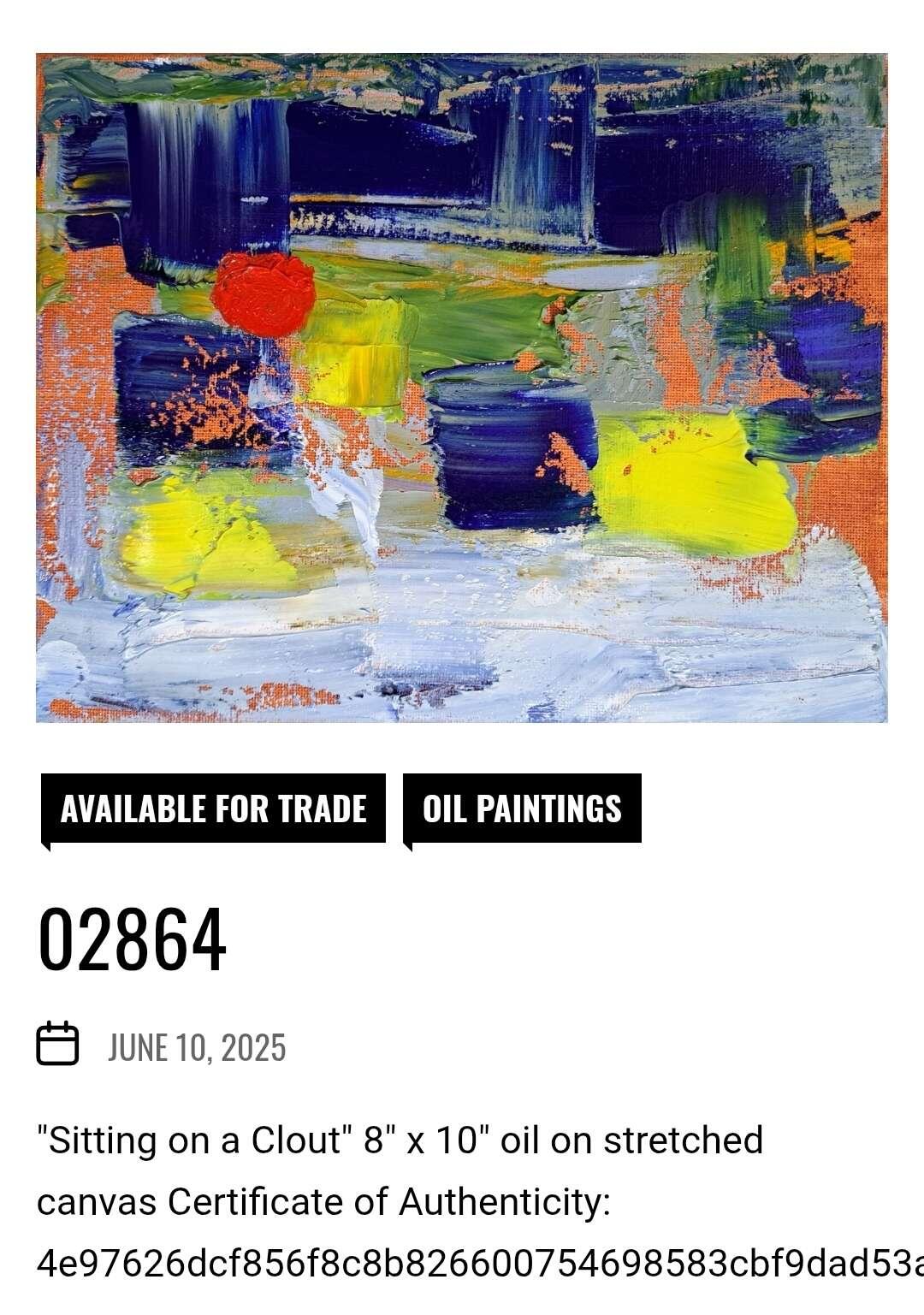
#art

3514a280:3894a480
posted
6 hours ago
As I watch the public protocols/platforms implode under bots and fomo (fear of missing outrage), the more convinced I am that focusing on specific crises as we are facing during extreme change, and abandoning a stress on identity, is a valid application for streaming logical maps.
597b651f:349ece8f
posted
7 hours ago
I #vibecoded a Tor-compatible desktop client for Routstr.
🏆 Get access to the best AI models—including ChatGPT, Claude, Grok, and many others—for every budget. No personal info, no monthly subscriptions. Starts as low as 500 SATS (~50 cents). 🛑 100% censorship-resistant.
⚡ Pay-per-use • Lightning & Cashu, pay only for what you use
🔐 Zero KYC • Private signup via Nostr, keep your identity hidden
🌐 Decentralized • Independent providers, no central control
🕵️ Anonymous • Tor integration masks your IP
📝 Source code here => https://github.com/alexandre-pecorilla/pyRoutstr
#AI #Bitcoin #eCash #Cashu #Lightning #LLM #Nostr #Routstr #ArtificialIntelligence
https://blossom.primal.net/c05f9af2f4432f886d42496e72fc3897ac28010b0f67390ab8d3e21ae56baeac.mp4
1c197b12:242e1642
reacted
7 hours ago
:eyes:
beejay
reposted
8 hours ago
{"id":"e4e73d4d921de8259a7b8d9edca59b76dc7a68f723eb4f912565aa97480cdeee","pubkey":"67ada8e344532cbf82f0e702472e24c7896e0e1c96235eacbaaa4b8616052171","created_at":1749599792,"kind":1,"tags":[],"content":"My son injured himself shitting and became a man today at the age of three years old. The turd was so large and ornate it was like the Stygian key to a demon city. He has been exorcised and will take is place in the hall of kings.","sig":"4aad9b59727d90ef0de8d56bee8306cbcbf9666f20259d750a9c084844954d8c0ed239444550bab90b670159f771dc536fc4139d6a22cc33ea191df69035fe79"}
0f42c61e:980064d6
reacted
8 hours ago
🤙