13bc95d9:9d80897d
posted
4 months ago
GM


c5337187:a5f35224
posted
4 months ago
🔔 Some Website Paid Bitcoin To Users !
📤 Number of Outputs: 4
💸 Total Amount Paid Out: 3.15215403 BTC
https://blockchair.com/bitcoin/transaction/dbced2b25be4d8b2e6aed5fd06698799d57cf98178417a18d92c2102fdccd02e
#bitcoin #crypto #wallet
jb55
posted
4 months ago
welcome!
Mir
posted
4 months ago
Let's make low time preference replying (not always replying immediately) great again.
You can reply from a place of awareness you get over time and not reactively, prioritizing what really matters to you.
Also, many things tend to be solved by themselves over time :)
But since we expect nowadays to get immediate responses, it's great (for education and respect) to tell we're taking some more time because we care for that, or because we have other priorities
Karnage
posted
4 months ago
Yeah. Could introduce sliding scale pow. But probably need a variety of different spam blocking mechanisms.
a3505d47:ca5a0e60
posted
4 months ago
Wow! Those look like warmer waves this am. Beautiful 🙌
The Fishcake🐶🐾
posted
4 months ago

b93049a6:9ab69d30
posted
4 months ago
GM
Free yourself from fiat slavery. Study #Bitcoin 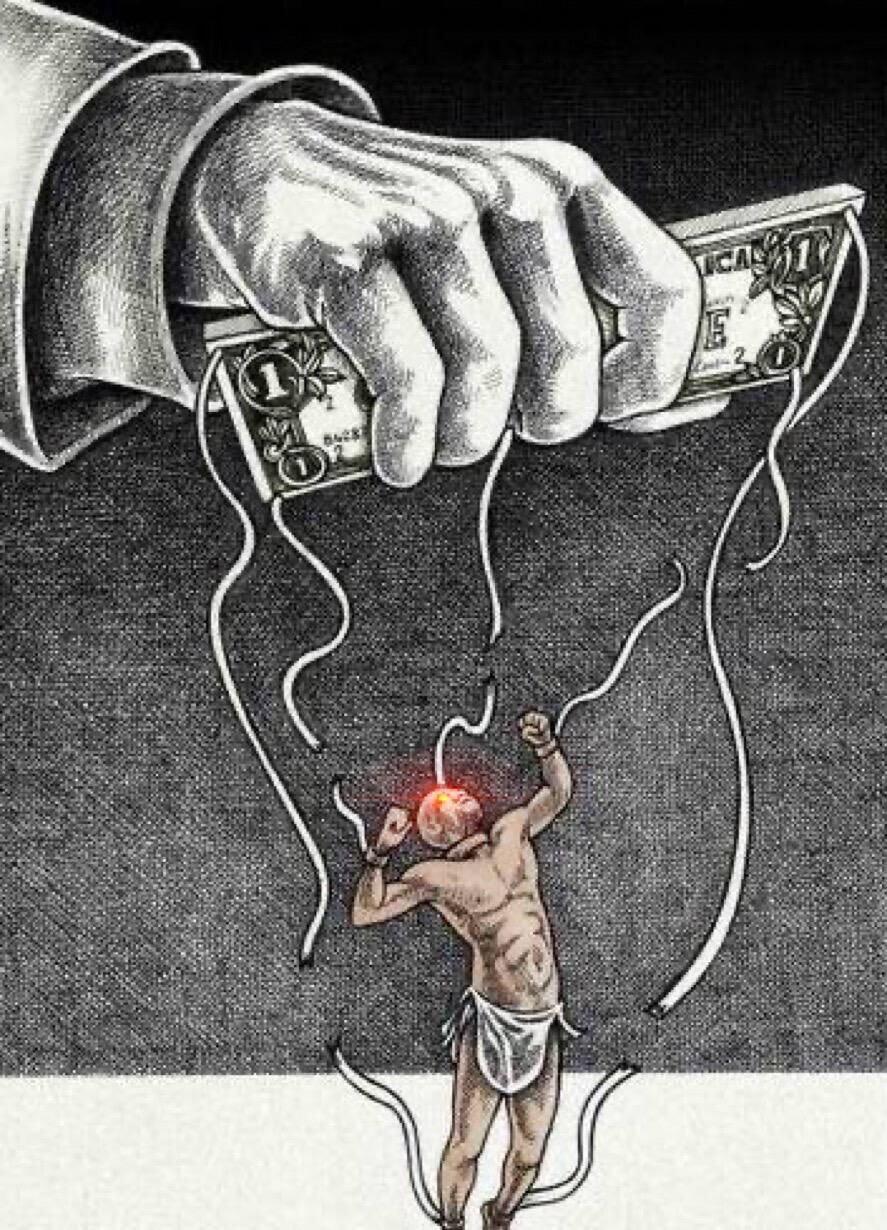

7ca66d41:0a388ca3
posted
4 months ago
Have you read “The Beginning of Infinity” by David Deutsch?
c5337187:a5f35224
posted
4 months ago
Crypto Will See Revolution By Acceleration ✍️ 2025 will see a sea change in the U.S. regulations, acceptance of bitcoin as digital gold and stablecoins as important rails for payments, says EY’s Paul Brody.
🔗 Read : https://www.coindesk.com/opinion/2025/01/02/crypto-will-see-revolution-by-acceleration
#bitcoin #news
9bfa99b4:ec2326eb
posted
4 months ago
That makes sense. Thanks buddy🫂
7ca66d41:0a388ca3
posted
4 months ago
We are the 0.000001%
We might not want to be, but we are destined for it.
Karnage
posted
4 months ago
ChatGPT gave me this
If you want to mitigate spam without relying on authentication, KYC, or CAPTCHA, you’ll need to focus on mechanisms that operate passively or are transparent to legitimate users while still making spamming costly or impractical. Here’s how you can achieve this:
1. Advanced Rate-Limiting
• Sliding Window Rate Limiting:
• Instead of fixed limits (e.g., 6 posts per minute), use a sliding window that dynamically adjusts based on user behavior.
• Example: If a user sends 2 posts in 10 seconds, slow them down further (e.g., increase delay between posts).
• Adaptive Rate-Limiting:
• Increase the delay for posting if users exhibit behavior indicative of spam (e.g., repeated patterns or high frequency).
• Legitimate users won’t feel this as they rarely approach limits.
2. Proof-of-Work
• Require clients to perform a lightweight computational task (e.g., solving a hash puzzle) before each post.
• Use libraries like hashcash to implement this.
• Adjust difficulty dynamically:
• Low posting rates = easy tasks.
• High posting rates = harder tasks.
• Spam becomes resource-intensive, especially for distributed attacks.
3. Behavioral Analysis
• Use heuristics or machine learning to detect spammy behavior without blocking legitimate users:
• Look for repeated similar messages from the same IP or across multiple IPs.
• Detect patterns like burst activity (sudden spikes in message rate).
• Analyze time intervals between messages to identify automation.
• Temporarily ban or throttle suspicious activity.
4. IP-Based Techniques
• IP Fingerprinting:
• Track patterns associated with specific IPs, such as frequent message submissions, and temporarily ban offenders.
• Soft IP Limits:
• Enforce progressive throttling based on message volume:
• First 10 messages per IP are free-flowing.
• Further messages introduce delays or are queued.
• IP Rotation Detection:
• Use reverse DNS lookups or IP clusters to detect rotating proxies.
• Block ranges of IPs if they’re part of spammy networks (e.g., TOR exit nodes, known VPNs).
5. Message Content Filtering
• Duplicate Message Detection:
• Block or flag identical or nearly identical messages being sent repeatedly.
• Spam Keyword Detection:
• Maintain a list of common spam phrases, URLs, or patterns, and filter messages that match these.
• Natural Language Processing (NLP):
• Use a lightweight NLP model to detect unnatural or spam-like messages (e.g., repeated links, excessive characters).
6. Reputation-Based Throttling
• Assign reputation scores to connections based on their behavior:
• New connections/IPs get stricter rate limits initially.
• Over time, if no suspicious activity is detected, the rate limit relaxes.
• Track reputation at the IP level and across message patterns.
• No need for explicit user accounts or authentication.
7. Delayed Backoff
• Introduce progressive delays for repeat submissions:
• First 3 messages are instantaneous.
• After 3, introduce a delay of 1 second, then 2 seconds, etc.
• Legitimate users can tolerate slight delays, but spamming becomes impractical.
8. Honeypots
• Create invisible fields or endpoints that only bots will interact with.
• If a client interacts with these, automatically block them.
• Example: A WebSocket endpoint that bots mistakenly try to send data to.
9. Token Bucket System
• Assign tokens to each connection:
• Each message consumes a token.
• Tokens regenerate at a fixed rate (e.g., 1 token every 10 seconds).
• Spammers will exhaust tokens quickly, while legitimate users will naturally regenerate them.
10. Statistical Pattern Recognition
• Analyze activity across the entire relay:
• Detect unusual traffic spikes.
• Identify message patterns repeated across multiple IPs or regions.
• Use these insights to automatically adjust throttling rules.
11. Geofencing or Regional Restrictions
• If spam primarily comes from certain regions or IP ranges, apply regional throttling or outright block those regions.
• Legitimate users from allowed regions won’t notice any impact.
12. Content-Based Delays
• For certain types of content (e.g., messages with links), introduce submission delays or extra processing time.
• This discourages spammers while minimally affecting legitimate users.
Final Strategy Without KYC, CAPTCHA, or Authentication
• Combine multiple approaches, such as:
• Rate-limiting (adaptive or token bucket).
• Behavioral analysis (detect patterns or anomalies).
• Proof-of-work for high-volume senders.
• Content filtering for duplicates or spam keywords.
This layered approach makes it resource-intensive for spammers while remaining transparent for legitimate users.
a3505d47:ca5a0e60
posted
4 months ago
Newfoundland Canada.
I hiked about an hour to this spot.
be2735cf:00813004
posted
4 months ago
#hola buen lunes de #Reyes a todos
Disfrutemos del dia y del tesoro oculto para muchos que es #bitcoin 



jb55
posted
4 months ago
Yes the goal of the main damus relay is free for use by everyone (with reasonable spam limits)
manlikekweks
reposted
4 months ago
{"content":"\nhttps:\/\/m.primal.net\/NUAb.jpg","sig":"39dafe5ba06abaad087a46a7af6871b193bf0f04af36b781020d8149a297ae9d7c6c9663d016b56a3ebb219106808626c3f1f864578e04e8ada34e3b3466cd3b","id":"36bf9f364864fe3bceeea8cac6c1024fb26a681b2fa1a67fc3ef7ae96517affd","pubkey":"f8e6c64342f1e052480630e27e1016dce35fc3a614e60434fef4aa2503328ca9","tags":[["e","6bf259527bccfe7286ad75f9e33070b61d175e69837870c0f5f811aa97f2825c","wss:\/\/multiplexer.huszonegy.world","root"],["p","90d9080b825ff98e9bb60f5735ff7ee5c5db6267ab93a3ec7b1d5d30374bba8a"]],"created_at":1736125122,"kind":1}
Karnage
posted
4 months ago
That would keep most people out :(
jb55
posted
4 months ago
I’m still confused why my relay has anything to do with this, why don’t they use their own relay? Unless they do it based on picking a single relay from your relay list. Maybe need to mark which one is your inbox relay and they would use that instead ?
Karnage
posted
4 months ago
Could also pow requirement on all notes. Low enough to not slow posting significantly but introduces an expense to spammers.
a3505d47:ca5a0e60
posted
4 months ago
GM to all who celebrate. 🎉
Loved watching the ocean flex it’s might yesterday. https://video.nostr.build/f0575b4e657f0f009c9866f98a560ae4bdc681598610930354b1c4ac230b147b.mp4
9a3281a7:d9248dc5
posted
4 months ago
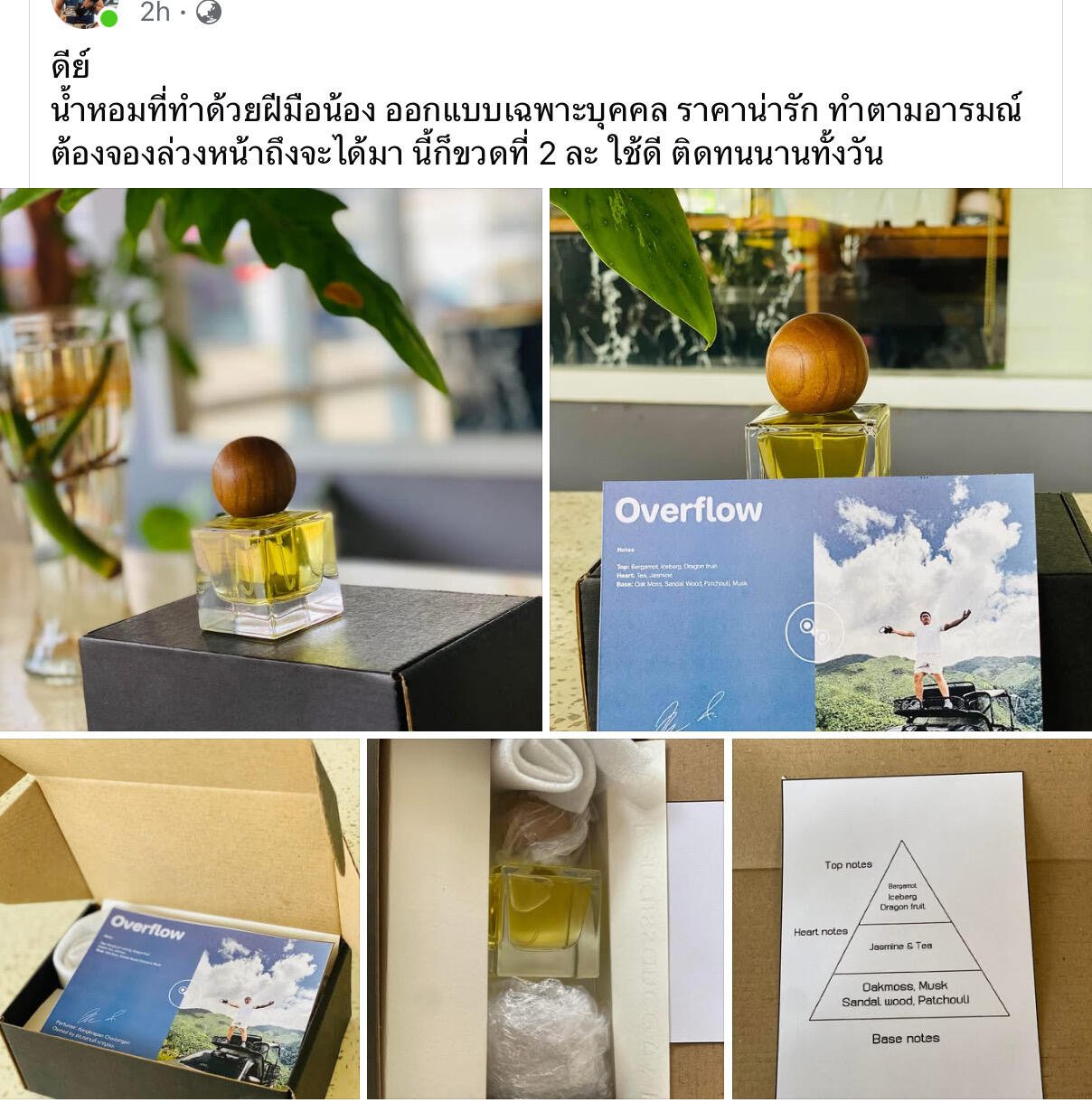 ปิดจ๊อบ น้ำหอมราคาแพง 🤣 ปี 2567
…
เข้าปีที่ 3 ที่เปิดทำน้ำหอมเฉพาะบุคคล
เป็นปีที่ไม่ค่อยได้รับออเดอร์ใหม่เพราะทำเคลียร์คิวยาว ๆ
เป็นปีที่ปรับราคาขึ้น 2 รอบ เพราะสู้ราคาวัตถุดิบไม่ไหว
บวกกับต้องลงโครงการขุดค้น
ทั้งปี ทำไป 23 ขวด 🙏
…
ปีนี้ว่ากันใหม่ เดี๋ยวจัดการตารางแล้วมาเปิดรับ รับน้อย ๆ เน้นดองงาน 🤣จะได้ทำอีกหลายโปรเจค
#Siamstr #ตลาดทุ่งม่วง #zap #Bitcoin #perfume #Nostr
ปิดจ๊อบ น้ำหอมราคาแพง 🤣 ปี 2567
…
เข้าปีที่ 3 ที่เปิดทำน้ำหอมเฉพาะบุคคล
เป็นปีที่ไม่ค่อยได้รับออเดอร์ใหม่เพราะทำเคลียร์คิวยาว ๆ
เป็นปีที่ปรับราคาขึ้น 2 รอบ เพราะสู้ราคาวัตถุดิบไม่ไหว
บวกกับต้องลงโครงการขุดค้น
ทั้งปี ทำไป 23 ขวด 🙏
…
ปีนี้ว่ากันใหม่ เดี๋ยวจัดการตารางแล้วมาเปิดรับ รับน้อย ๆ เน้นดองงาน 🤣จะได้ทำอีกหลายโปรเจค
#Siamstr #ตลาดทุ่งม่วง #zap #Bitcoin #perfume #Nostr
Karnage
posted
4 months ago
What about captchas 🤔 make them fill those out 🤣
4a916109:b0c26f86
posted
4 months ago
 #wales #rhondda #home #history #monochrome #nostr #bitcoin
#wales #rhondda #home #history #monochrome #nostr #bitcoin
54bab130:020f26ba
posted
4 months ago
The goal should be: Every year, less and less money buys more and more products and services.
#bitcoin